A Weak Password Lost a Company $50,000
Imagine a hacker coaxing you into transferring $50,000
Well, it happens all the time
This blog is based on a real case that itro worked on to resolve. In summary, a small Melbourne based company lost over $50,000 AUD due to a weak password policy. For privacy reasons, let’s call them ‘Acme Widgets’.
Summary:
- Acme Widgets became victim to spear-phishing due to a weak password policy, the company lost over $50,000
- itro recommends strong passwords policies, if you are not receiving prompts to change your password about every 6 months, contact us immediately.
- Phishing is a form of computer specific social engineering in which an attacker disguises as a legitimate source to trick the user into handing over sensitive information. 1
- This article talks specifically about spear-phishing. This is a targeted attack towards a specific person or organisation. This is different to phishing, a large scale attack where a malicious email is sent to thousands of users.
The run-down
- How spear-phishing works
- How did a company lose $50,000
- Why is it bypassing anti-spam mail filter solutions
- What itro is doing to prevent spear-phishing
- What you can do to prevent email spam attacks
1. How spear-phishing works
The attack involves three phases:
Phase 1: A phisher gains access to a victim’s email inbox (usually through a password attack or a phishing attack – the latest phishing emails scams here)
|  |
Phase 2: Now the phisher has access to an employee’s email account, they will monitor the email account and watch for emails containing words such as “payment”, “statement” or “invoice” or “deadlines”.
|  |
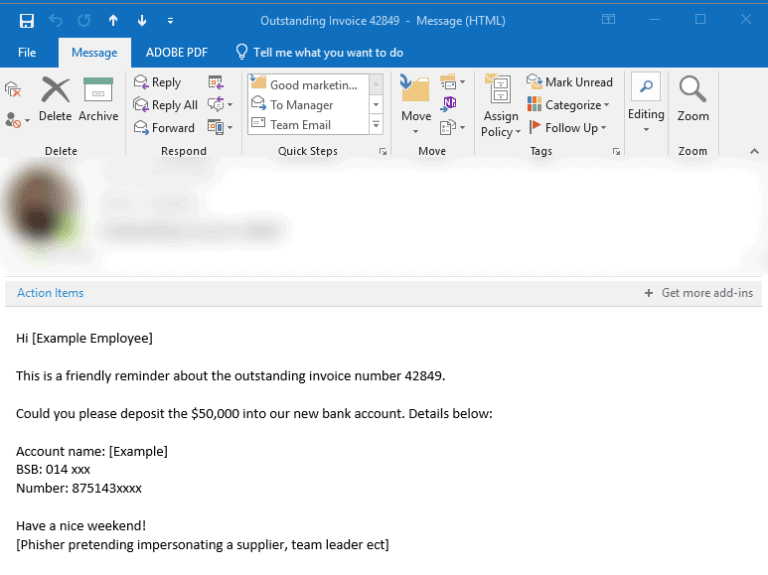
Phase 3: This is where the hacker becomes incredibly cunning. Once details on a payment deadline are identified, a hacker sends an email to the victim masquerading as a firm, client, manager or supplier reminding an individual of their due payment date or to confirm details. Except! They notify you to transfer to a different banking account. An example is below:
| |
2. How Acme Widgets lose $50,000
The victim, the Operations Manager working for Acme Widgets, had their email account compromised, either from a password attack (by brute force – passwords are attempted over and over again until accessed is gained; or a dictionary attack – passwords are tried against a list of weak common user passwords), or by a phishing attack (e.g. an email is sent containing a malicious link that directs the victim to enter their email username and password to open an attachment, which is then sent to the attacker).
Once the attacker gained access to the victim’s account, the phisher created a mail transport rule re-directing any emails containing the subject “statement”, “payment”, and “invoice” to the attacker’s account rather than the victims’ inbox.
The attacker intercepted an email between the victim and one of their supplier’s regarding payment for goods. With this information, the phisher created multiple fraudulent email accounts that looked identical to the supplier’s account, but with extra letters – easy to overlook if you do not view the senders address regularly.
Next, the phisher sent an email requesting funds to be transferred to a new bank account and because the email looked identical, the victim assumed it was an authorised email and sent the funds to the phisher rather than the supplier.
The case was reported to the police, however, the company will most likely not recover the lost funds.
3. Why is it bypassing anti-spam mail filter solutions?
Spear-phishing emails generally make it past the filter because they contain no suspicious content or malicious links. The email address will be from a registered domain causing no red flags. Some of these attack types will still attempt to deliver the usual trojans/crypto via a compromised URL or document attachment).
Typically, phishing emails, a broader type of attack, do not enter your mailbox. If an email comes through, make sure to click, at the bottom of the email, ‘Report this message as spam’.
4. What is itro is doing to prevent spear-phishing
Password policies
- Last year itro implemented password policies across all organisations. Passwords must contain an uppercase, lowercase, number and special character. If you have not being prompted to change your password in 6 months, please contact us.
Multi-factor authentication (MFA)
- We use and recommend MFA for our Office 365 accounts
- What is multi-factor authentication? It is a security system that requires more than one method of authentication. For example, if I attempt to log into my outlook from a new computer, I will need a code that is generated from an app on my phone (the app is Authenticator).
- Is MFA something that interested you? Contact us on 1300 10 1000 to discuss.
5. What can you do to prevent email spam attacks
Verbal clarification
- Encourage your Accounts team to ring and verbally qualify any unexpected email requests for money supposedly sent by a supplier, client, senior team leader or internal department before making a transfer. Even if a follow-up call causes annoyance, that is a far better option than having to tell management about an incorrect money transfer! Be especially cautious of any payment requests or changes to existing payment requests
Good security starts with your password!
- Security experts recommend using a password manager. A password manager assists in generating complex and secure passwords and avoids using weak ones. We suggest using a password manager like Dashlane or LastPass but here is a list of password manager products in the market.
Employee education
- User training and education for common cyberattacks and prevention methods
- Do not open suspicious emails containing malicious links or attachments
- Checking a sender’s address matches with the original sender
- Language style – if the writing style suddenly changes, or suddenly contains poor English and grammar, beware!
Stop worrying whether you are next target for an attacker and contact itro for a FREE security IT Assessment today.
Contact Us Today
Call itro on 1800 10 3000 or email [email protected] to chat with one of our experts on how we can assist you with your IT needs and to receive your FREE IT assessment.